Secure Your Business's Future & Peace of Mind: Enterprise Cyber Protection at SMB-Friendly Prices
Empowering Small Businesses with Comprehensive Cybersecurity Solutions
Is your business prepared for the unexpected?
Introducing our "Always-On Guard" Protection Plan: 24/7 digital defense that serves as your business's personal cybersecurity bodyguard and designed to seamlessly integrate into your operations.
CORE BENEFITS
24/7 Constant Protection: 'Always-On Guard' never sleeps. It's your relentless shield against unforeseen dangers, keeping your operations safe 24/7.
Comprehensive Digital Defense: Our wide-reaching protection means your business is secure - from tricky scams to harmful software, we've got you covered.
Affordable & Easy-to-Integrate: Always-On Guard Plan offers straightforward, cost-effective security for SMBs—quick setup, no hidden fees, just seamless, comprehensive protection.
SUBSCRIBE TO LEARN MORE.

Activate Your Comprehensive "AOG" Unified Foundation
Protection Plan Today
Start Your 14-Day Risk-Free Data Shield - Licenses Starting at $129 for a Single User
Guard What's Priceless: Your Peace of Mind. Kickstart your cybersecurity journey with our core "Always-On Guard" Foundation Protection Plan. Dive into comprehensive digital defense and discover why businesses trust us—all with a 14-days comprehensive, risk-free cybersecurity trial. Experience the difference committed protection makes.
Simplify your security with one AOG Foundation license that covers your devices —phones, laptops, network, tablets —streamlining protection and delivering peace of mind.
Tailor your cybersecurity strategy by adding specific Compliance Add-ons, available for separate purchase, ensuring a perfect fit for your business needs.
Further empower your team with immersive simulations and gamification, elevating cyber awareness and safeguarding your company’s future.
Everything Begins with a Strong Foundation

"Always-On Guard" (AOG) Foundational Protection Plan – 24/7 Cybersecurity
The "Always-On Guard" Foundational Protection Plan acts as a 24/7 digital bodyguard for your business, protecting your data from hackers, viruses, and cyber threats. This plan is the cornerstone of your cybersecurity, offering continuous, comprehensive protection in an evolving threat landscape.
With sophisticated security measures, "Always-On Guard" ensures your data is always safeguarded, providing peace of mind and reliable defense against digital attacks. Trust the AOG Plan to keep your business secure and resilient.
One Minute Explainer Video
Enterprise-Grade Cybersecurity, Tailored for YOU at Unbeatable Prices
Your One-License Gateway to Complete Cybersecurity Peace of Mind
Protect Up to 5 Devices with Unmatched Simplicity & Affordability using our Unified Foundation Protection Plan.
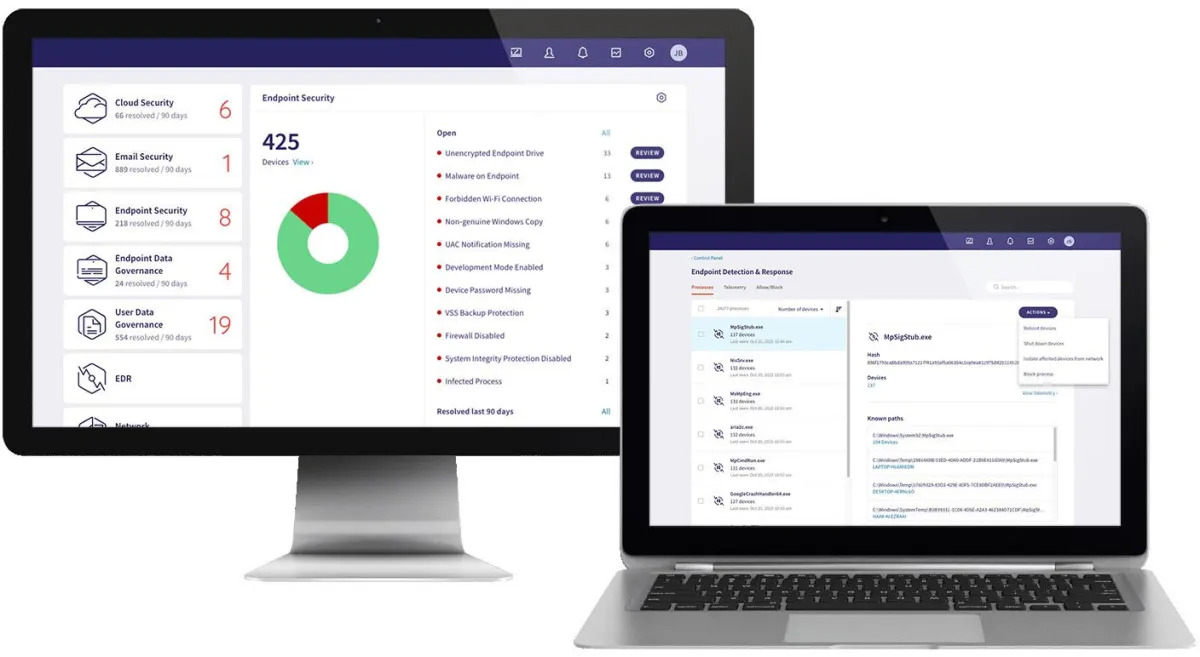
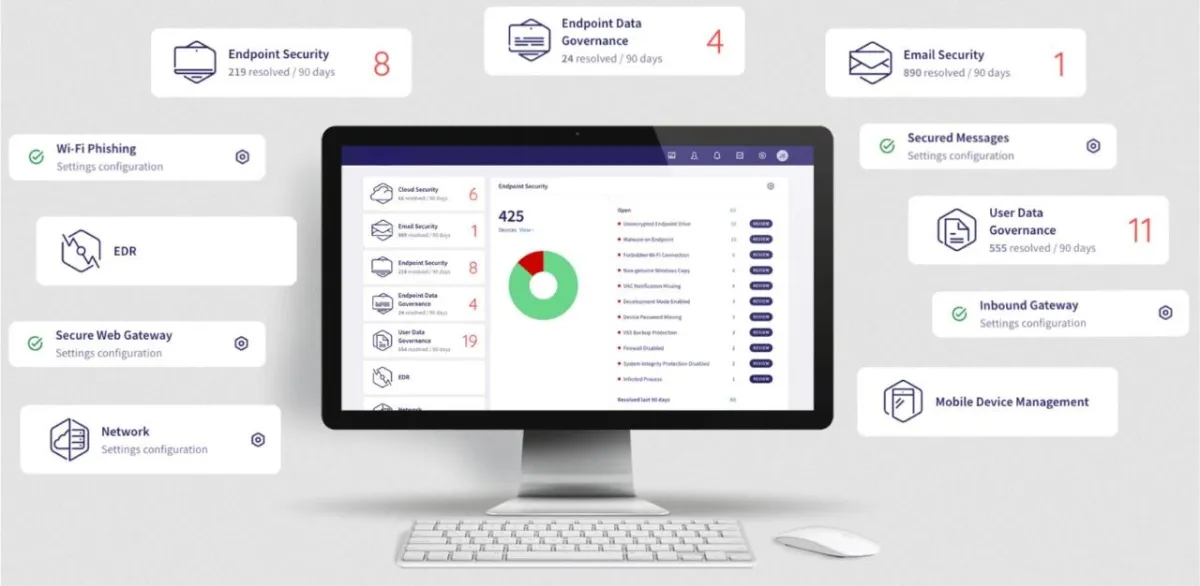
Simplify Your Cybersecurity Needs With a Single Solution
From securing emails to protecting devices — all under one manageable package in our Unified Foundation Protection Plan.
A Trusted Shield in a Digital World of Uncertainties
Using our Foundation Protection Plan safeguards everything from personal conversations to work data with our 14-day, risk-free trial, experiencing a new level of digital safety that’s within easy reach.
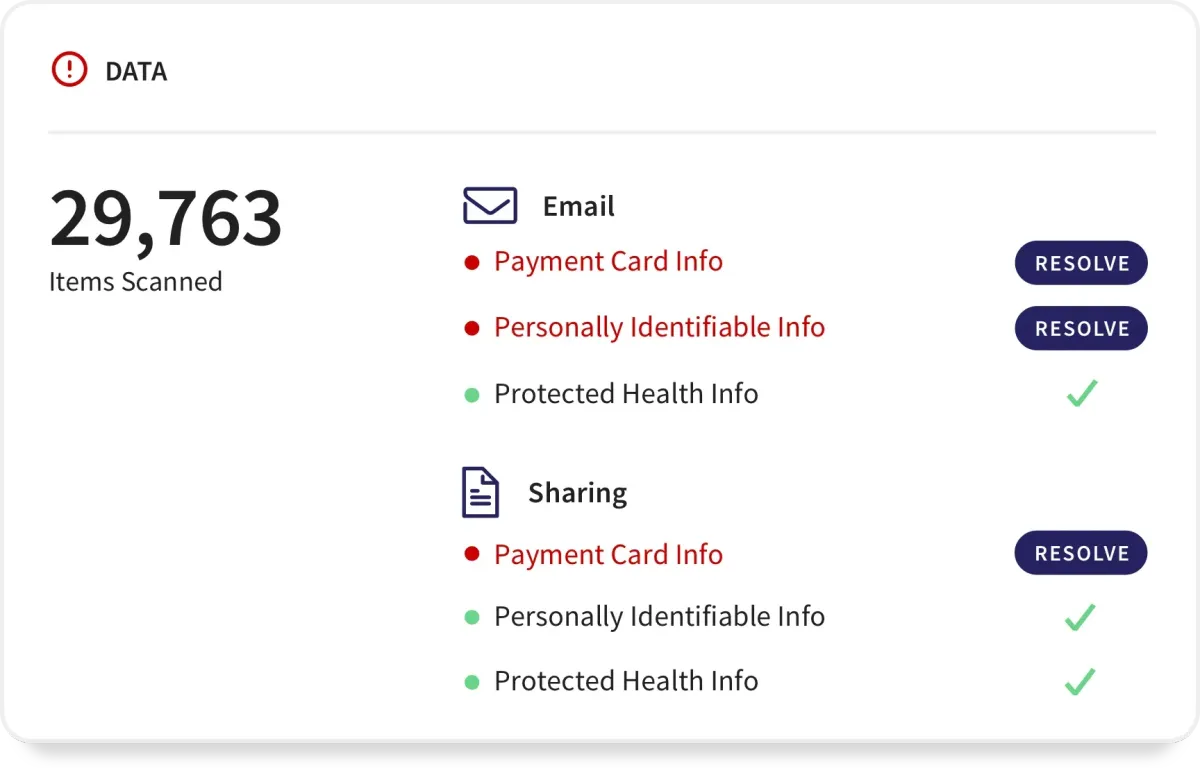
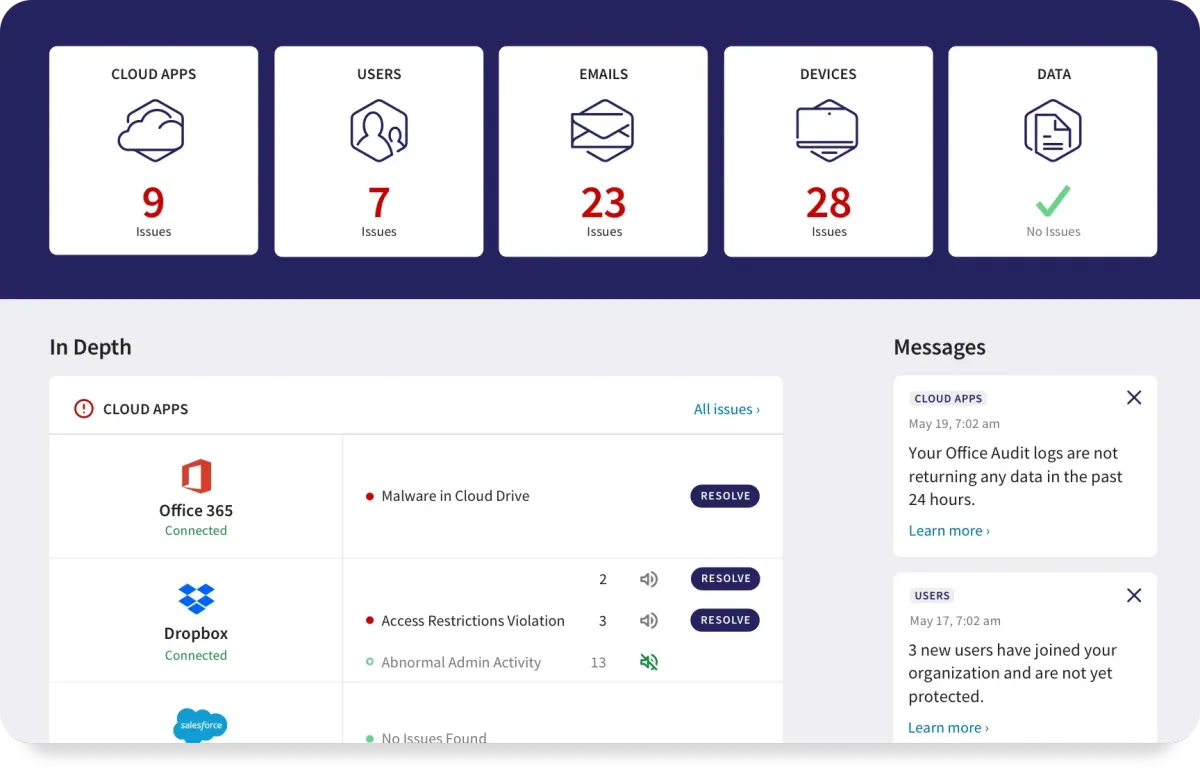
Discover A Unified Foundation Protection Plan For Comprehensive Protection
Toggle personalized security at your command: Our suite includes everything from advanced antivirus and email protection to network defense and data governance, all customizable to ensure your digital world remains secure.
"Always-on Guard" Foundational Protection Plan
Cyber Secure Online's Transparent Pricing Scale
(Slide the scale to the number of Users for "per user" pricing.)
Our pricing can scale to one millions users upon request. Schedule a call to learn more.
We are pleased to offer a 20% discount for annual plans.
Why Choose Us Over the Rest?
Always-On Guard Offers Comprehensive Protection at Unbeatable Value For Just $129/user/month
Discover the unparalleled cybersecurity features and unmatched affordability of our solution, designed for
businesses seeking robust protection without complexity or hidden costs.
OUR COMPETITIVE ADVANTAGE
FEATURES
CSO's Always-On Guard
CrowdStrike
SentinelOne
Bitdefender
Endpoint Security (Next-gen AV)
✅
✅
✅
✅
Email Security (Malware, Phishing)
✅
$$
$$
$$
Cloud Security (O365, GSuite, etc.)
✅
$$
$$
$$
EDR (Endpoint Detection & Response)
✅
✅
✅
$$
Network Security (VPN, Firewall)
✅
$$
$$
$$ Partial
Data Governance (Endpoint, User Data)
✅
$$
$$
❌
WiFi Phishing Protection
✅
❌
❌
❌
Inbound Email Gateway
✅
❌
❌
❌
Secure Web Gateway
✅
$$
$$
$$
User Data Governance
✅
❌
❌
❌
Pricing (per user/month)
$129
$160+
$160+
$110
✅ Included | $$ Requires Add-On | ❌ Not Available
Sources: CrowdStrike, SentinelOne, Bitdefender, Comparitech & Trust Radius
Key Advantages
No Hidden Costs: Unlike others, we provide comprehensive cybersecurity, including email and cloud security, without requiring you to spend more on add-ons.
Exclusive Features: Benefit from unique protections like WiFi phishing prevention and inbound email gateway—features you won't find with our competitors.
Transparent Pricing: While others start at $160+ with less included, we offer everything your business needs for just $129/user/month.
Ready to secure your business with our all-in-one solution?
For the best viewing experience, please rotate your device to landscape mode.
Why Choose Us Over the Rest?
Always-On Guard Offers Comprehensive Protection at Unbeatable Value For Just $129/user/month
Discover the unparalleled cybersecurity features and unmatched affordability of our solution, designed for
businesses seeking robust protection without complexity or hidden costs.
Discover the unparalleled cybersecurity features and unmatched affordability of our solution, designed for
businesses seeking robust protection without complexity or hidden costs.
OUR COMPETITIVE ADVANTAGE
FEATURES
CSO's Always-On Guard
CrowdStrike
SentinelOne
Bitdefender
Endpoint Security (Next-gen AV)
✅
✅
✅
✅
Email Security (Malware, Phishing)
✅
🔒
🔒
🔒
Cloud Security (O365, GSuite, etc.)
✅
🔒
🔒
🔒
EDR (Endpoint Detection & Response)
✅
✅
✅
🔒
Network Security (VPN, Firewall)
✅
🔒
🔒
Partial
Data Governance (Endpoint, User Data)
✅
🔒
🔒
❌
WiFi Phishing Protection
✅
❌
❌
❌
For the best viewing experience, please rotate your device to landscape mode.
Inbound Email Gateway
✅
❌
❌
❌
Secure Web Gateway
✅
🔒
🔒
🔒
User Data Governance
✅
❌
❌
❌
Pricing (per user/month)
$129
$160+
$160+
$110
✅ Included | 🔒 Requires Add-On | ❌ Not Available
Sources: CrowdStrike, SentinelOne, Bitdefender, Comparitech & Trust Radius
Key Advantages
No Hidden Costs: Unlike others, we provide comprehensive cybersecurity, including email and cloud security, without requiring you to spend more on add-ons.
Exclusive Features: Benefit from unique protections like WiFi phishing prevention and inbound email gateway—features you won't find with our competitors.
Transparent Pricing: While others start at $160+ with less included, we offer everything your business needs for just $129/user/month.
Ready to secure your business with our all-in-one solution?
Do You Need Even More Cybersecurity Protection?
SEE BELOW
In today's digital landscape, comprehensive cybersecurity extends beyond foundational protections. For organizations looking to elevate their security posture to the next level, we offer a suite of advanced cybersecurity enhancements designed to fortify every aspect of your digital operations:
Additional Compliance & Policy Management: Simplify compliance with industry regulations through our tailored policy management tools, ensuring your business meets all necessary standards without the hassle.
Customized Training Programs: Equip your team with the knowledge they need to be the first line of defense against cyber threats with our interactive training modules and security awareness programs.
Phishing Gamification: Engage and educate your employees using our innovative phishing simulation games, turning potential security risks into informed defenders of your network.
Dark Web Monitoring: Proactively protect your business from data breaches with continuous monitoring of the dark web for stolen credentials and company data, securing your information before it's exploited.
Dark Web Monitoring: Proactively protect your business from data breaches with continuous monitoring of the dark web for stolen credentials and company data, securing your information before it's exploited.
Domain & Email Protection Services: Safeguard your digital identity with comprehensive domain protection, preventing unauthorized domain transactions and mitigating the risk of domain phishing attacks.
Are you ready to take your cybersecurity to the next level and ensure your organization is prepared for any threat?
Additional Compliance, Policy, Training, Phishing Gamification "Add-ons"
Optimize Your Security Posture By Making Your Employees Your First Line of Defense... by
transforming staff from potential risk factors into proactive protectors against cyber threats.

DataSafe Compliance Training Standards
Customized DataSafe "Legal" Shield security to achieve audit-ready proof of compliance and policy driven cyber awareness training.
Equip your team with the knowledge to identify and avoid cyber threats through easy-to-understand training sessions, making your employees the first line of defense against digital attacks.

Identity Theft and Scam Guard
Vigilant protection against impersonation and cyber threats blending Domain "Doppelganger" Protection and Email Threat Alerts.
Safeguard your business’s and customers’ identities from being stolen or used in scams, keeping your reputation intact and your operations secure.

Proactive Dark Web
Monitoring
Our Secret Web Watchdog service keeps you a step ahead by vigilantly monitoring the dark web's hidden corners for any signs of threats or stolen data concerning your business. It proactively alerts you to potential issues before they escalate, providing unparalleled security for companies of all sizes.
Quantum "Q-Day" Encryption Protection
Preparing for Tomorrow’s Threats Today: Classical encryption methods are vulnerable to attacks by quantum computers.
We are diligently fine-tuning our processes to bring you cutting-edge cyber defense and communications mechanisms to withstand quantum computing threats.
Additional Compliance Add-ons
Optimize Your Security Posture: Enhance Your Foundational Cyber Protection with Targeted Compliance Add-ons

DataSafe Compliance Training Standards
Customized DataSafe "Legal" Shield
security to achieve audit-ready proof
of compliance and policy driven cyber awareness training.
Equip your team with the knowledge to identify and avoid cyber threats through easy-to-understand training sessions,
making your employees the first line of defense against digital attacks.

Identity Theft and Scam Guard
Vigilant protection against impersonation and cyber threats blending Domain "Doppelganger" Protection and Email Threat Alerts.
Safeguard your business’s and customers’ identities from being stolen or used in scams, keeping your reputation intact and your operations secure.

Proactive Dark Web
Monitoring
Our Secret Web Watchdog service keeps you a step ahead by vigilantly monitoring the dark web's hidden corners for any signs of threats or stolen data concerning your business. It proactively alerts you to potential issues before they escalate, providing unparalleled security for companies of all sizes.

Quantum "Q-Day" Encryption Protection
Preparing for Tomorrow’s Threats Today: Classical encryption methods are vulnerable to attacks by quantum computers.
We are diligently fine-tuning our processes to bring you cutting-edge cyber defense and communications mechanisms to withstand quantum computing threats.
Get Ready with Our "Customized" Compliance Bundles
With new rules on the horizon like the Corporate Transparency Act, staying compliant is key to your business success. Our "Customized" Compliance Bundles, paired with Always-On Guard Foundational Plans, are designed just for this. They include DataSafe Compliance, Domain and Email Threat Alerts, and Deep Web Cyber Threat Surveillance — everything your small business needs to meet compliance easily and affordably, beyond the basics. Set for 2024, thrive with us by being more than prepared.
SEE WHAT OUR CLIENTS ARE SAYING...
Join the Revolution: Unify Your Cybersecurity with Cyber Secure Online
Secure your business's future with Cyber Secure Online; a one-click, award-winning, and flexible cybersecurity solution that grows with you, eliminating the need for multiple vendors and ensuring top-tier protection effortlessly.

Simplified Integration
Snap-together modules simplify your cybersecurity, ensuring easy deployment and management through a single platform.

Unified Interface
A single, intuitive dashboard allows for swift navigation, event response, and status assessments, streamlining your security operations.

Enhanced Endpoint Agent
Ensure your business remains unscathed from the costs of digital vulnerabilities. One endpoint agent delivers multiple layers of protection.

Integrated Data Engine
An AI-driven, interconnected data engine enhances module communication, optimizing your security posture without the need for manual integration.
Unmatched "Digital Shield" Cybersecurity: Why Us?
Custom-fit Security: Solutions as unique as your business and practice.
"Always-On Guard" Support: Immediate help, any hour, for when IT emergencies strike.
Ahead of Threats: Continuous security updates keeping data safe.
Effortless Power: Robust cybersecurity made user-friendly for all staff.
Informed Decisions: Expert cybersecurity advice tailored to your needs.
Privacy First: Highest standards in data protection for confidentiality.
Cost-Effective Security: Exceptional safeguarding that fits budgets.
Cyber Attacks: A Question of When, Not IF !
AROUND-THE-CLOCK
24 x 7 x 365
MONITOR DETECT RESPOND
PROTECT YOUR DATA + REPUTATION
Empower Your Business with Unmatched Cybersecurity Confidence
At Cyber Secure Online, we dismantle the barriers between small to medium enterprises (SMEs) and robust digital protection. Our mission is to democratize access to top-tier protection, ensuring that every business, regardless of size or budget, can defend itself against the ever-evolving threats of the digital world.
Why Choose Us?
Affordable Excellence: Unlock the gold standard in cybersecurity with our Digital Health Check. We’re committed to making world-class security accessible, offering SMEs the same level of protection and peace of mind as industry giants.
Streamlined Simplicity: Your time is valuable. That's why our process is designed to be as straightforward as it is secure. From the get-go, a single, integrated form covers everything from NDAs to payment, setting you on the fastest track to comprehensive digital security without the hassle.
Expert-Guided Compliance: Navigate the maze of cybersecurity regulations with ease. Backed by our deep expertise in crucial security standards—NIST 800-53, FISMA, FedRAMP, FIPS-199—our programs, services and consulting help you meet and even exceed regulatory benchmarks, embedding compliance into the fabric of your security strategy.
Collaborative Partnership: Cybersecurity isn’t a one-size-fits-all solution. We offer a hands-on, collaborative approach, inviting your insights and inquiries at every stage. Your active role guarantees a tailor-made security posture that aligns perfectly with your unique business needs and goals.
Our Promise to You:
Secure your enterprise with Cyber Secure Online and our partners embracing the future with confidence. Beyond shielding your business, we empower you to thrive in the digital age, safeguarding not just your operations, but the trust of your customers and the integrity of your brand.
Fortifying Digital Frontiers: Your Bridge Over Cyber Breaches
PRIVACY POLICY | © 2024 Cyber Secure Online LLC | All Rights Reserved

